I’m fascinated by real-world events more than fictional stories. So, I chose to read about North Korean cyberattacks by investigative journalist Geoff White. The book proved to be a lot better then I anticipated! And I did anticipate it to be really good! I did not have too much knowledge about North Korea in general, but I knew that it has been an active Nation State threat at least since early-2010’s. In this post I’m going to go over the chapters and the reason why I liked the book so much. Let’s start!

Chapters
Here are the chapters of the book:
- Jackpot
- Going Broke
- Superdollars
- Dark Seoul
- Hacking Hollywood
- Fallout
- Chasing the Joint
- Cyber-slaves
- The Getaway
- Baccarat Binge
- The Plot Unravels
- The Las Vegas of the East
- WannaCry
- Old Tricks, New Money
- Going Back for More
I will be summarizing the content and plot of the book below while also adding some of my own thoughts in between.
Spoiler Warning! Reading this blog post will absolutely reveal the main events described in the book!
Chapters 1-4
First chapters of the book taught me a lot about North Korean history, culture and the mindset of the regime that was formed after the Korean war. It also extensively describes the supreme leaders starting from Kim Il Sung and moving on to Kim Jong Il. For someone like me who’s never visited North Korea or Asia for that matter, it’s captivating to read how totalitarian and controlled North Korean society is. After reading the first few chapters it felt like a place where the regime is practicing a mind control experiment and keeping it’s citizens in line by controlling the access to food. Of course it became abundantly clear that North Korea has been a poor country for most of its modern existence. This fact is actually the reason that has sparked the events that the book is written about. Most events later in the book take place at the time when Kim Jong Un is already the leader of the regime.
Before the dawn of modern technology and high-speed internet connections North Koreans tried solving the extreme poverty by counterfeiting US dollars. And they became surprisingly good at forgery, to a point where those “superdollars” where almost indistinguishable from genuine dollars. When the rest of the world caught up what was going on they enforced sanctions against North Korea. This only deepened the famine among the already hungry nation. North Korean geography is partly mountainous and the soil is not ideal for farming, so achieving self-sufficiency is very hard.
During the Kim Jong Il era, the digitalization started to emerge which he embraced and which his son, Kim Jong Un, has taken to a next level. The book explains that access to computers, let alone to internet, for most North Korean is unheard of. Only the elite, which the most gifted hackers belong to, are trusted with the access to outside world; using public internet and foreign work assignments. This equals one thing: any cyber attack originating from or traced back to North Korea, is most certainly government organized operation. This makes North Korea a nation state actor at the stage of a global cybercrime.
At the fourth chapter the author Geoff describes how unforeseen hacking groups with confusing names took responsibility for hacking South Korean broadcasting networks and some banks. This was in 2013 when Kim Jong Un had risen to power. Looking back at this chapter after reading the whole book, it seems like these operations were the initial spark for the hidden hacker army of North Korea. Like a baptism of fire using a military slang.

Chapters 5-6
Chapters ‘Hacking Hollywood’ and ‘Fallout’ will describe in detail how (allegedly) North Korean cyber operations hacked Sony Entertainment using fake social media accounts, phishing and ultimately; malware in 2014. This happened because Sony was involved with producing a movie called ‘The Interview’ where North Korean leader, Kim Jong Un, is depicted with his own name. The plot of the movie is that an American journalist (played by James Franco) gets to interview Kim Jong Un with his producer with him (played by Seth Rogen), but during the interviewing the two decide that they want to assassin the North Korean leader. In the end of the movie the assassin plan is carried out and Kim is portrayed dying in a fireball. Apparently the movie did not please North Korean regime. Reading these chapters, I must admit that for a brief moment I forgot that I wasn’t reading an entertaining novel, that this actually happened. This case seems to be well covered and there’s multiple views to it from the Sony Entertainment personnel, the FBI, the US government and the people involved in the movie.
Eventually Sony Entertainment data was leaked all over the internet, which resulted in massive financial damage to Sony Entertainment and many former employees personal data was also leaked among all data leading to identity thefts which made it really hard to continue normal life. Digital infrastructure was damaged badly as much of data was wiped, before leaking it. It was a total disaster, but lead FBI on tails of the hackers responsible of the attack.

Chapters 7-9
These chapters go over how North Korean cybercriminals prepared a Billion-dollar heist against an Bangladeshi Bank which took over a year for them to prepare. These chapters were really fu–ing frightening to read. It shows how vulnerable the global banking system SWIFT was at least back in 2015-2016. I can only hope that it has gotten substantially more secure. Criminals hacked the bank and went undetected for a year while navigating in the banks network. They got the initial foothold through the bank’s HR department, then moved laterally escalating privileges, establishing backdoors and compromising more powerful accounts all the while erasing any breadcrumbs behind them. Once the right time had come, they started sending money transfer requests to US Federal Reserve Bank where the Bangladesh Bank had around $1B in dollars. Due to the global time zones and different national holidays and differences in weekends (in Bangladesh weekend is from Friday to Saturday) the hackers maximized the time window they had and managed to get $101M dollars transferred. $81M went to a small Filipino bank’s branch office.
There is a chapter in between the heist story that ties the FBI and North Korean hacker named Park Jin Hyok, who still has his picture and information on FBI’s most wanted website at the time of writing. This is a fascinating story where suddenly FBI realized that the fake accounts used in the Bank heist are the same or have similarities to the fake accounts used in the Sony Entertainment hack. The accounts are peeled layer by layer ultimately uncovering a real human being, a North Korean who now could be prosecuted. It goes to describe how North Korean hackers are sent abroad, treated like military with very strict discipline, kept on a short leash and paid just enough to keep them going. Reading it made me somewhat feel sorry for them as it seems that the only way to escape the inherited North Korean class system, Songbun, is to become good at sports, math or arts. For kids that are talented in math, the road leads to serving the government as a hacker. The living conditions in these abroad hacker dorms are not glamorous, far from it. Why are they sent abroad? Because North Korea has really few IP addresses, so any malicious activity is easily traced back to them, but also to experience and learn about the culture and behavior of the outside world which they have no idea until they actually experience it outside North Korea. This experience is valuable for the hackers to be able to do social engineering and phishing.

Coming back to the bank heist story, chapter 9 tells us how the accounts in the Filipino bank got established, how the stolen money was received to the accounts and what actions did the bank’s branch office take upon the large sums of money received. It goes on further to explain the Philippines Senate special hearings of the bank, the bank’s manager and the money exchange company which was used to cash out the money ($81M) and reveals some of the accomplices of North Korean regime. Someone was sent to jail, but the hackers’ are still left untouched at this point. As the technical hack of the heist is already behind us, the story dives into the world of money-laundering.

Chapters 10-12
In chapter 10 we continue to read about the interesting world of casinos and money-laundering. Gambling in China is illegal and therefore Philippines has established a strong foothold as a destination for Chinese high-rollers. About $30M dollars from the $81M was handed to a mysterious Chinese man after the money was changed into a huge pile of cash. The rest, $51M, headed towards two different casinos. If you’re not familiar with casinos and how they operate, this chapter will teach a lot. The closest I’ve been to a casino was watching ‘Ocean’s’ movies starring George Clooney. The term ‘junkets’ will become familiar. They are private rented rooms inside casinos where high-rollers play and which are operated by different companies other than the casino. What raised my eyebrows was the part where seemingly all over the world the heist was already covered by all the major news media and the Philippines Senate and the Bangladesh Bank was closing in on the stolen money, basically knowing that it was being “washed” at the tables of two casinos: Solaire and Midas. But those casinos considered that its clients were not criminals, pled for confidentiality and so the money-laundering operation kept going under everyone’s eyes. At the time, in 2016, casinos in Philippines did not have a money-laundering policies. And again the most of the stolen money got away, but some of it, around $16M, was recovered.
Chapter 11 takes us on a hunt for the remaining $20M which did not go to Philippines. A Sri Lankan journalist Shihar Aneez bumped into the case by accident and soon realized that the case he was digging was a part of something lot bigger. Again I learned more about money-laundering tactics and how foundations and charities are used for money-laundering. They are perfect for it as there’s usually large sums of donations coming from random donors globally. That was the case here too. A Sri Lankan woman, a serial-entrepreneur who had not made her break-through yet, started a foundation which was almost immediately used for moving the North Korean heist money. There were ties to shady character from Japan who donated a large sum of money, which was actually the Bangladesh Bank heist money. A Sri Lankan bank was luckily awake and considered the transactions suspicious and eventually returned the money to Bangladesh.
Last but not least, the book takes us on a journey to Macau, which is an Asian Las Vegas. Actually we should say that Las Vegas is American Macau because, as stated in the book, Las Vegas’ commercial revenue in 2019 was $9 billion compared to Macau’s $35 billion. It goes on to describe the dark past of Macau and how Kim Jong Il’s son, Kim Jong Nam, ended up living in Macau after being fallen off from the pecking order to become the next ruler of the ‘Hermit Kingdom’ (North Korea). Jong Nam was assassinated at a Malaysian airport by two women, who will tell an amazing story how they ended up on such operation. At the time, Kim Jong Un, his half-brother whom he had no relationship whatsoever, had already risen to power. Many believe that North Korea was behind the Jong Nam assassination (which North Korean regime disputes) as Jong Nam had for some years given critical comments about North Korean regime to journalists. The book revealed connections from all central characters of the events from Sri Lanka, Japan and Philippines including to Chinese men who aided with the money-laundering in Philippines and ran away with the stolen money and North Korean regime to Macau.
Chapters 13-15
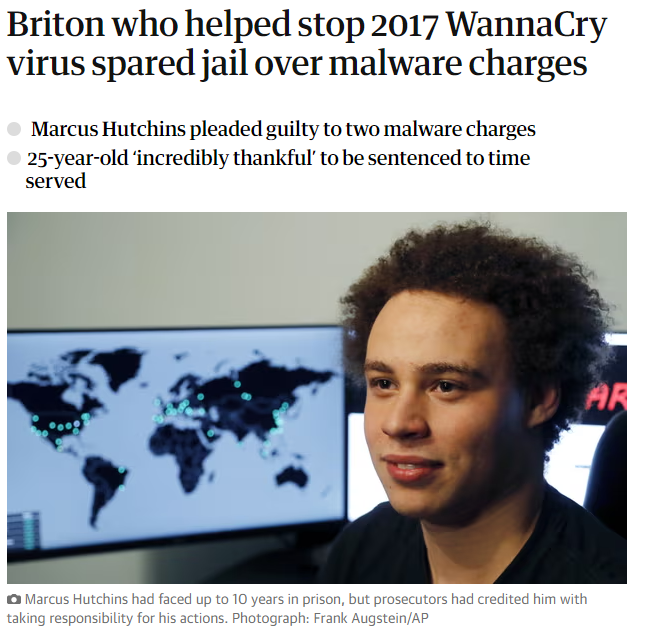
The last three chapters of the book takes us to the world of cryptocurrencies, the new skill North Korean government hackers started to master, after the Bangladesh Bank heist had showed that laundering tangible fiat money like US dollars or Philippine pesos is a lot of work, lot of middle men which all have to paid, inevitably narrowing down the profit margin. WannaCry case described in the book reveals just how dangerous malware development can be and how different, some unexpected, parties are trying to find vulnerabilities and keep those found a secret from the public and do not disclose them with the vendor. This might not surprise, if you think that these are hackers doing this, but it might surprise if I’d say these would be government agencies too. WannaCry was an example of what might happen, if you try and keep a vulnerability as a secret for yourself to use, but instead, it might end up in the wrong hands and be pointed back at you. It also tells an amazing story of how a young malware specialist living with his parents stopped the global outbreak of WannaCry epidemic, which later helped him to avoid prison time in United States as he was visiting DEF CON in Las Vegas and got arrested.
During years 2017-2018 North Korean government hackers finessed how they would hack cryptocurrency exchanges and adapting to their ever tightening security controls and money-laundering policies. While cryptocurrency has some anonymity to go along with it, changing cryptos to fiat money to launder it is still a risky move. Pulling out your stack of cryptos after any hack would also set alarms in crypto exchanges so they had to come up with a technique called “peel chain”. They essentially automated how they exchanged small amount of cryptos to fiat currency, moved all the remaining cryptos to another crypto wallet and repeated this over and over, thus avoiding the security triggers of the exchange. They also allegedly were involved in a Marine Chain crypto investment scam and they spread their own crypto trading software which, you guessed it, contained malware to steal all the coins from the user’s wallet. All the while doing these hacks, phishing has remained in North Korean’s toolbox and it has been their tool of choice many times over. There’s a story how a technician for a crypto exchange was sent a LinkedIn message for an open position that seemed like it was a perfect match with his professional profile. Of course, it was a lure targeted for him and it got him to open the application form which ultimately established a backdoor persistence to the company’s network, leading to the hack and heist of $75M equivalent in Bitcoin. The author estimates that if we use the value of the stolen cryptos at the time of hacks, then heists attributed to North Koreans sum up to a total of $1.3 billion!
Last chapter wraps up the stories by painting an image of what type of international crooks were North Koreans dealing with. Some are real hardcore criminals with lots of connections and experience of money-laundering, the types you would expect. But it’s surprising that some accomplices might be social media influencers you may have followed too!
Podcast
If you’re not a ‘book reading’ type person, then you might be delighted that BBC has published a podcast that you can find from Spotify (the massive link below) and BBC website. These podcasts have somewhat same information as the book but they also have some other topics as well.
Summary
This book was intriguing, even though the subject is crime, cybercrime, extreme poverty, extreme famine and totalitarian regime of North Korea. I’m an information junkie myself, and for me real-life stories are far more fascinating than fiction. I know that I will probably be reading this book again in some years. I recommend anyone even with no technical knowledge to read it because it opens your eyes about global cybercrime and global crime networks in general. Even thought some of the events were many chapters long and some were half a chapter they were all informative and expanded my world view. Some of the stories like WannaCry could have been explained in more detail, but I acknowledge that it’s my technical background that craves for technical juicy details. Most readers are fine without them. If you’re unfamiliar with the North Korean regime, system and society, there are well described in the book in general at some degree and comprehensively from a global cybrecrime’s and from a North Korean individual child, soon-to-be-government-hacker’s, perspective.