In this blog post I’m going to open my thoughts about five things from this year’s Digital Defense Report by Microsoft which they have been publishing since September 2020. Digital Defense Report is an annual report by Microsoft Security which today covers a broad range of cybersecurity topics like state of cybercrime, cybersecurity challenges, collective defense, nation state threats and security and resilience innovations. This year’s report is 131 pages long, but extremely interesting for any security analyst, any Chief Information and Security Officer or any technology architect. There is an “executive summary” -style condensed report available for those in hurry, called ’10 essential insights from the Microsoft Digital Defense Report 2023′. Let’s start!
1. Microsoft’s global security footprint is massive
This one might either be a total surprise or very self-evident depending who’s reading this, but Microsoft’s security efforts are very notable and anyone not seeing Microsoft as a leader in cybersecurity estate should really take a second look. I haven’t been paying close attention to Microsoft’s security offering, their security research and their efforts to stop nation state actors for more than a couple years now. But even I’ve noticed that there’s been a huge development from 2019 to 2023. Just this timeframe. Just four years.
Let’s look at the numbers stated in the report, shall we?
10,000 security experts
Work titles range from engineers, researchers, analysts, data scientist, threat hunters, investigators to cybersecurity experts. That’s a lot of experts; more then most companies will ever have employees altogether.
65 trillion signals a day
With a help of AI of course, these experts will analyse (I had to use calculator here) 2,372,500,000,000,000 signals a year and the number is not decreasing. If I round the number up, that is 2.4 quadrillion signals per year. I’m not blaming them for using AI, because there is no chance that any company could hire enough people to go through that amount of signals.
15,000 security partners
There’s probably a vendor somewhere that has more global partners than 15,000 but for Microsoft this is just their security partners. I’m not sure how this number is calculated, but I assume these partners have to have at least Security Solution Partner Designation or even one of four Security specializations. But it’s obvious that when this amount of partners drives Microsoft’s security suite globally to the customers, and those solutions get adopted it feeds back to those trillions of signals that Microsoft gets to deal with daily. Popularity of those solutions also begs another business on a side which is training all those partners to Microsoft’s security stack.
Tracking over 300 threat actors
The sheer volume of threat actors does not initially give away a wow-effect until you stop to think ‘how’? Monitoring the actions of nation state actors, ransomware groups and other advanced persistence threats (ATPs) is not easy, as most of those groups will go great lengths to conceal whatever they’re doing. Those trillions of signals are part of it, of course, but there is more investigation, threat hunting and geopolitical analysis that goes into this work.
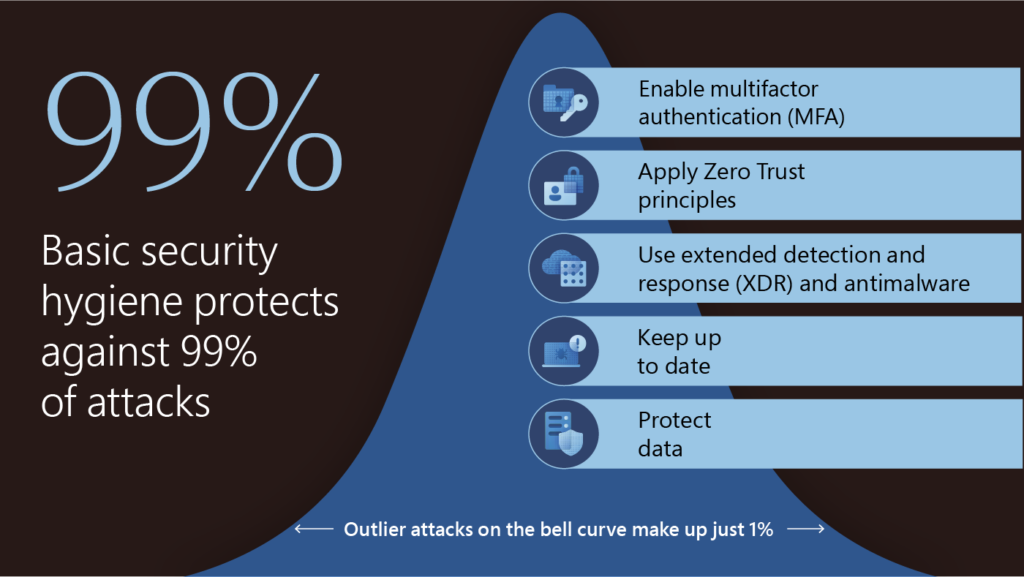
2. Good old basic security is still as valid as ever
This one hits hard for multiple reasons. As the security field is moving forward and fast, new solutions emerge and new features get developed, there’s still that same old box of used-up toys that no one wants to play with. You know all those unsexy things everyone used to do 8 years ago like patching software, firmware and drivers, like configuring a sensible access control lists throughout you systems and adapt to least privilege access, like creating a good backup practice that is periodically tested for restore, because there’s no backup unless you test that the backup can be restored, like configuring firewall rules, like deploying a working anti-virus agent, like configuring system and application logging based on business needs and the most recent overused toy that already gets folks yawning when mentioned: MFA. By no means I’m saying that this stuff should not be taken seriously, quite the opposite actually. The point I’m making is that it is very easy to get side-tracked on some new and shiny stuff even if the foundation is still uncomplete.
But there’s a silver-lining here: If that list is not yet complete on your organization, most of those will not generate any additional licensing cost or maybe not even competence upskilling to complete. Just prioritize and focus your effort to configure and test the configuration. There’s an old saying that “if you’re hunted by a lion, to survive you don’t have to be the fastest zebra on the herd, just faster then the slowest one”. Similar thinking works here at some degree. As long as the cost for an attacker is higher than the cost of breaching a company next to you, you might just be safe. For now at least. But don’t put your feet on the table if you’ve got all of the basic building blocks of security in place already, because just as the digital estate changes over time, so must the protection of it keep up to it.
3. Ransomware attacks keep increasing
Human-Operated Ransomware (HumOR) attacks have been growing ~200% from September 2022.
If the magnitude of cybercrime has not yet settled in, consider the early days of ransomware, where a malware affected a single endpoint, encrypted files or disks and demanded a ransom to be paid. And now consider that there are over a hundred known ransomware-as-a-service affiliates. Cybercrime is crime, but cybercrime is a huge global illegal business also. Report estimates that HumOR attacks will continue to grow in 2024. As an upside to all this, organizations with solid security posture are well equipped against these attacks and likelihood of an attack succeeding is very low. But as defenders get better at defending, attackers keep getting better at attacking, and this has resulted in remote encryption during HumOR attacks. When encryption is done remotely, it disarms defenders and their process-based remediation. Attackers are minimizing their footprint during an attack to evade defense.
As an IT administrator of an organization you should be aware that most HumOR attacks attempt to gain access to unmanaged or BYOD devices, because they lack the enterprise protection of managed devices. A staggering 80-90% of all successful compromises derive from unmanaged devices. And based on what we just learned it’s not a good news that the primary victims of ransomware attacks during the past year has been small and medium size companies and organizations, where perhaps BYOD-culture and ‘not-yet-managed’ devices gets more easily overlooked.
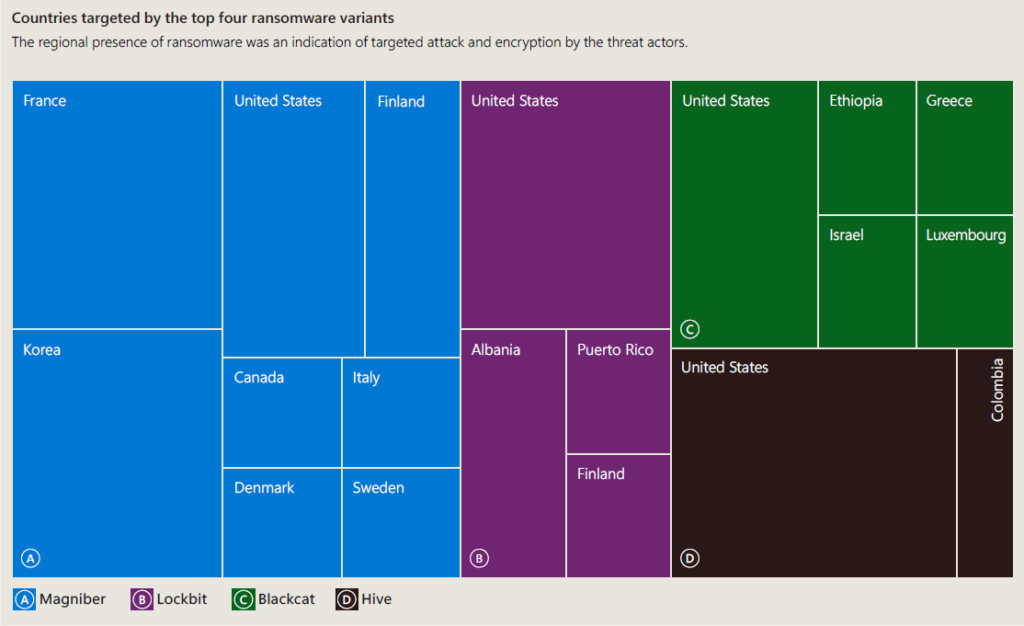
On the below diagram are four top ransomware malware variants. Magniber being an automated variant, Lockbit, Blackcat and Hive being human-operated. As a Finland native, it catches my attention that a small country from up north is represented here amongst United States, Korea and France, but perhaps it has something to do with Finland becoming a full-member of NATO on April, 2023.
4. The scarcity of cybersecurity professionals
There has been steady discussion of shortage of security professionals for at least 3-4 years now. First of all, the IT field as a whole needs more women to be involved. There are male-dominant professions in the infrastructure and agricultural field that don’t attract most women. Information Technology is often seen as one of those male-dominant fields and for sure, it is. I think the demographic distribution in the software development show more women than other aspects of IT. But to be fair, if I omit the statistical fact that most women are more interested in people rather than things, and more men are interested in things rather then people, there is no other explanation why women should not rush into the cybersecurity field. And I’m sure women will do just as fine as their male counterparts, because I don’t believe this profession requires a male personality traits.
Secondly, as briefly mentioned in the first section, AI helps us to analyse security signals. It must also keep helping the defenders even more in the future because we, as humans, cannot scale infinitely. The finite resources and finite space in this globe does not allow it. So we need AI, and we need it to be on our side. Microsoft has just released their Security Copilot for Early Access Program and we’ll see how we can leverage the power of AI in cyber defense in 2024.
Thirdly, cybersecurity education and training must be ramped up by educational institutions, businesses and governments. I would include some basic security training in the elementary school as well, because kids of younger and younger age are using social media and messaging apps and need this guidance. Maybe some of those kids will find this stuff interesting and end up defending your organization some day. There are also retrain programs for adults that want to or need to change professions for whatever reason. Those should also be utilized and offer more security related trainings.
5. Local accounts remain as a security risk blind spot
The report describes a term Return on Mitigation (ROM) as the relativity between how much effort you need to put into a mitigation and how high or low the return of it is. Consider the following quote from the report.
Generally speaking, the lower the resources
and effort involved, the higher the return on
mitigation (ROM). As an example of a high return,
consider a simple solution to implement context
based MFA protection. This solution is highly
effective in preventing initial access (high security
value) but very simple to implement (low effort)
When implemented, this solution effectively prevents
initial access by providing more context around the
authentication attempt, such as geographic location
and the application used. The additional context
can be combined with requiring the user to enter
a number (number matching) to complete MFA to
further improve sign-in security.
‘Insufficient protections for local accounts’ is listed as 12 on return on mitigation on a scale to 0 to 15, so quite high. But the percentage of customers with the issue is a whopping 60%! As a consultant, at the same time this breaks my heart, but also re-enforces the understanding that there is a lot of work to do in the basics still. Not too long ago Microsoft published an successor to legacy Microsoft LAPS, Windows LAPS which targets this issue.
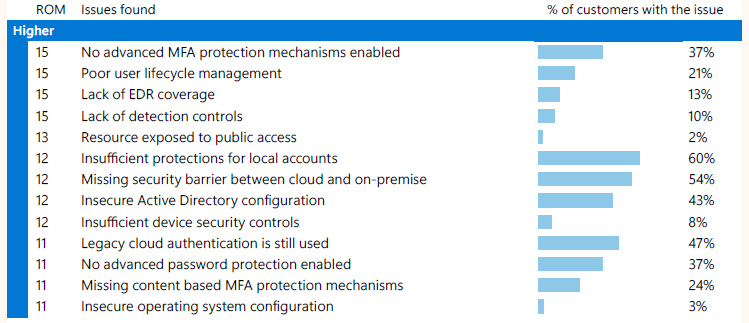
If we go back to the topic no. 2 about good old basic security, local accounts have also persisted on every administrators ‘things-to-secure’ -list for a long time. To me, this is not surprising, but I’m hoping more people read these reports and act upon the hidden gems that we’re offered for free. ‘Missing security barrier between cloud and on-premise’ is another security creep that organizations that have hybrid environments need to address quickly. It only requires one bad network segmentation and a compromised endpoint for an attacker to gain foothold of your cloud environment via the on-premise networks. It’s every administrators nightmare to get a message late in the evening from a colleague or supervisor, that states that the whole network is not accessible and none of the accounts they have can login. It’s a feeling I don’t want to experience, but nevertheless will have to prepare for.
Summary
Microsoft Digital Defense report is awesome read and you don’t have to swallow it in one chunk. But if your responsible of your or your customer’s digital estate, security pro or not, this is a report for you! Remember to build your security posture foundation first with those basic security building blocks and then move on to more advanced security. The report is full of useful insights that can be put to a roadmap or prioritize over the current “this-and-that” you’re working on. Please also share the awareness of this report to your colleagues and managers. If they have hard time understanding why they should read it, you can tell them that there is a cost of inaction also and awareness never hurt anybody.
Depending on your field of business, you might also find yourself interested of those nation state actors that might be targeting just you.
Stay secure!

