In my previous blog post, titled Microsoft enforces tenant-level MFA in July! What should I know?, we looked at the upcoming change where Microsoft is enforcing MFA upon all user accounts logging in to Azure management tools. This enforcing of MFA with a short notice rang some bells in my head and then I remembered that Microsoft initially started the shaping up of MFA adoption already last November in 2023. Back then, Alex Weinert, the VP for Identity Security, wrote a long rant about MFA adoption followed by the announcement of Microsoft-managed Conditional Access policies. I wonder if the efforts for Microsoft-managed policies were not enough to ramp up MFA adoption or was it too little too late? The whole saga is looking like an uphill battle for Microsoft. Let’s start!

Setting the goal
In this blog post we’ll be looking at what are Microsoft-managed conditional access policies, when were they announced and what is the status today in June 2024. We will also do some thought work and speculation of the connection to the recent announcement made in May 2024 about enforcing the MFA upon all Azure users*
*No, not really all Azure users in the broadest possible sense, but that’s how it was announced initially
Microsoft-managed conditional access policies
Terminology: First of all, I’m making an executive decision to shorten the whole shebang to a term “Managed policies” from now in this post. You know…to save my time and your reading time.
Announcement, a bit of history and relation to Secure Future Initiative
The announcement of managed policies took place in November 6th 2023 which was just few days after Microsoft announced the Secure Future Initiative (SFI) in November 2nd 2023. Alex Weinert (Vice President for Identity Security) made a reference to the SFI announcement and these managed policies are part of the Microsoft’s bigger SFI ambitions.
The announcement describes how requiring MFA for Microsoft accounts (consumer identities) was a huge success that tilted all the percentages to right directions. There was fear that the MFA requirement would add too much friction and drive consumers away. That did not happen. But when Microsoft tried to replicate the success within the commercial market, enterprises using Microsoft Entra ID (it was Azure Active Directory back then obviously), nothing seemed to make any change.
2017: MFA utilization rate presented at Microsoft Ignite was 0.7% of monthly active users.
2018: Microsoft removed MFA costs for all customers and utilization rate disappointingly increased only to 1.8%
2019: Security Defaults saw the day light for the first time. It was on by default for new Entra tenants and more then 80% will leave it on.
2020: Pandemic restrictions hit us at global scale and remote work became the new normal. Utilization rate went up to over 25%
2022: Security Defaults are being extended into existing tenants. More than 94% of existing tenants will leave them enabled. This work is still continuing.
2023: Over 7 million tenants have been enabled with Security Defaults. If you have Security Defaults enabled, you experience 80% less compromises than a tenant which has it disabled. Security Defaults stack up to more then half of the MFA usage in Microsoft Entra. MFA utilization rate is over 37%
Late-2023: Microsoft-managed Conditional Access policies start rolling out to Entra ID tenants.
What policies are being rolled out?
Three policies have been created, but you might not see them all in your tenant because of eligibility targeting and license requirements. You should see at least the first one, that protects privileged sign-ins to Microsoft admin portals. This means Azure portal, Microsoft 365 admin portal, Exchange Admin center and so on.
| Policy name | Eligible tenants | Policy effect |
| Require multifactor authentication for admin portals | All customers | Covers privileged admin roles and requires multifactor authentication when an admin signs into a Microsoft admin portal |
| Require multifactor authentication for per-user multifactor authentication users | Existing per-user multifactor authentication customers (less than 500 enabled or enforced “per-users”) | Applies to users with per-user multifactor authentication and requires multifactor authentication for all cloud apps. Helps organizations transition to Conditional Access |
| Require multifactor authentication for high-risk sign-ins | Microsoft Entra ID Premium Plan 2 customers | Covers all users and requires multifactor authentication and reauthentication during high-risk sign-ins. |
Rollout is gradual and there is a 90 day window (now extended beyond 90 days since March 19th) for customers to review and modify policies before Microsoft turns them on. What I’ve seen is that most companies have opted out and turned off the managed policies. This is not to say that other companies would not have adopted them, because my sampling size is not that wide and is also geographically and possibly also security posture-wise biased.
While managed policies cannot be deleted they can be edited, to exclude users, groups or roles. Additionally, admins can edit the state of the policy and duplicate any of the managed policies to allow more changes to the policy.
Microsoft reserves the right to introduce new features or functionality to the policies over time. I mead, they are Microsoft-managed after all!
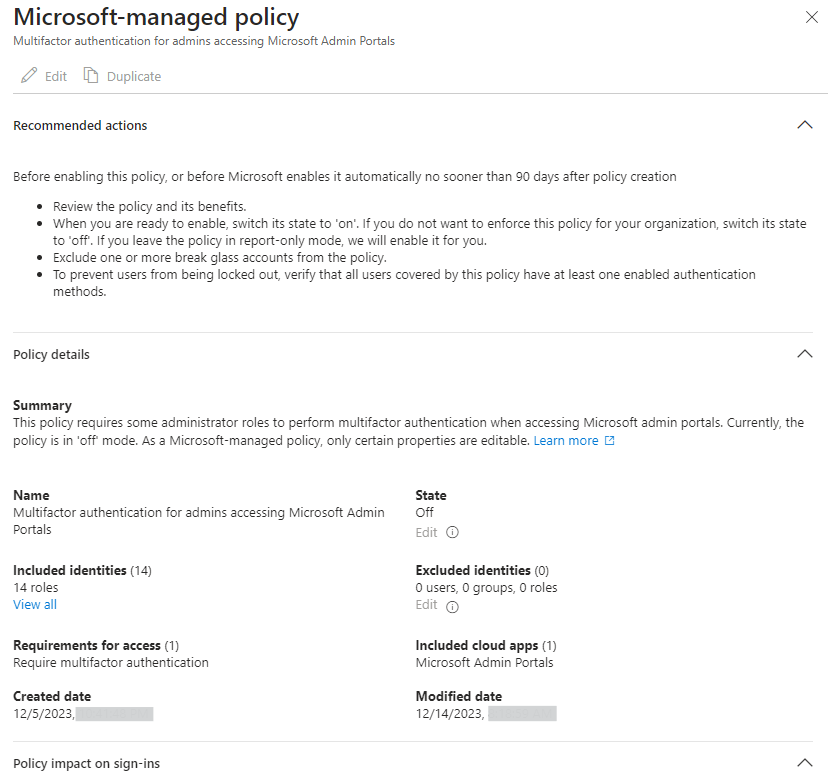
Where are we with managed policies?
There are promises that there will more managed policies and even some that are tailored to your tenant-specific situation. On March 19th 2024 Microsoft announced that they have rolled managed policies to more than 500 000 tenants. Furthermore, managed policies do not count towards the CA policy limit and if there is a policy that meets or exceeds the managed policy requirements then the managed policy will not be enforced. Also as stated above in the previous section the 90 day windows is not extended. Customers will receive email and Message Center notification 28 days in advance.
Development of Conditional Access
Managed policies will of course benefit from the number of feature updates that Conditional Access policies have received during the past year or so. These are the ones I can list on top of my head (some still in preview!) and there’s probably more:
- New What If… experience
- IPv6 support for Named Locations
- New CA policy templates
- New policy monitoring graph with filters
- New policy filtering on main policies blade
- New network conditions and options
- Insider risk condition
- Device filtering condition
- Authentication flows condition
- Authentication Strength grant control
- Token protection session control
- Global Secure Access security profile session control
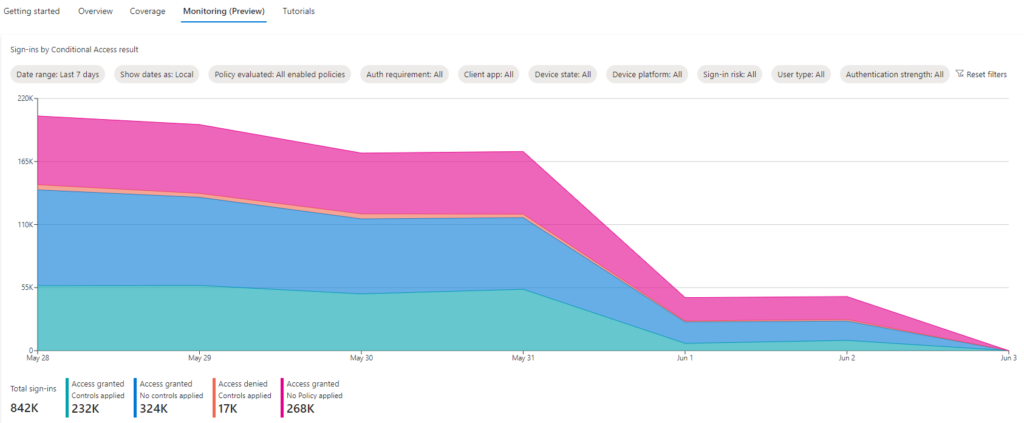
Reflecting on MFA adoption issues
After reading all the announcements and studying a bit of Microsoft’s MFA adoption history it’s not likely that they will give up on MFA adoption at the current below 40% utilization rate. All the evidence is pointing that they will come up with more severe enforcements like the one announced on May 14th 2024. I wonder if the soft approach with managed policies was too little too late and if the recent Microsoft breaches compromised something that is not told to the general public. I suspect that enterprise level companies who have licenses and have enabled Conditional Access have not adopted Microsoft-managed policies and it has not been the success story that Security Defaults has been.
May 14th announcement’s schedule for the upcoming change was only 45 days (at the time of writing 27 days left). We the customers have not seen this type of hasty changes, so something’s up and while I’m very much pro-MFA and support enforcing basic security configurations to some degree, I can’t help but feeling there’s something that’s not being told and Microsoft is trying to make quick corrective actions. I should also point out that the enforced MFA requirement that starts rolling out in July 2024 is not in a form of a conditional access policy, so it’s not customer manageable. To me this all smells like the managed policies were not success because customers could turn them off and thus weren’t adopted widely enough.
Summary
All in all, Microsoft-managed conditional access policies, while being a good idea, is probably doomed to fail unless there will be those tenant-specific AI-powered policies. Companies that have adopted Conditional Access usually already have existing policies that might overlap or interfere with the managed policies. MFA adoption and utilization needs to get closer to 90%, but this all taps into the bigger conversation that includes the MFA methods as well. Users should be enabled with authentication methods that are both secure and frictionless. FIDO2-based methods have been the most secure methods for a while now, but they still have some friction. Microsoft Authenticator passkey method which is in preview might be the answer, at least for the information workers carrying smart phones all day. In my books, Microsoft-managed conditional access policies are somewhat a lost chapter, but I’m hoping they prove me wrong!
Stay secure!
References
Auto rollout of Conditional Access policies in Microsoft Entra ID – Microsoft Community Hub