I needed to check what accounts I have in my YubiKeys and do some housekeeping to delete unnecessary accounts. I figured there has to be some way to do this and found out that Yubico has a nifty command line tool called YubiKey Manager that does exactly that. This isn’t a new tool and it has been around for years it seems, but don’t expect all people to still know about it so here’s a walkthrough of what I did to achieve my clean-up task. Let’s start!

Setting the goal
What I needed to do is simple. I have two security keys. The other one is USB-A key with liveness detection, so you have to type the PIN and then touch it to use the key. Pretty standard stuff. The other one is USB-C key with Biometric fingerprint detection. I wanted to check the accounts on both of them and register an additional finger to the biometric key. That’s all, nothing fancy, just cleaning up old accounts that I don’t use anymore.
YubiKey Manager installation
First you need to download YubiKey Manager. I’m using Winget to manage my software, you can also download YubiKey Manager from Yubico’s website. There’s desktop version and CLI version available. You don’t need both, but I ended up grabbing both of them.
After installation I have an unnecessary OCD habit of checking the version. You can do this with ykman -v
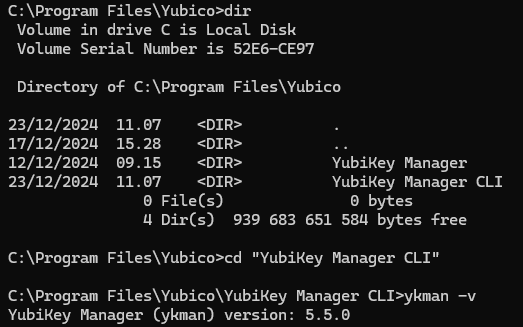
Had to double check that PATH was correct too so double check from the root of C:\
Everything good to go!
Checking general info and list existing accounts
So let’s move on to checking the accounts that we have in the security key. First I wanted to check the fido info command.
Notice that running these fido command require running them on an elevated Command Prompt or PowerShell, which ever you want to choose.
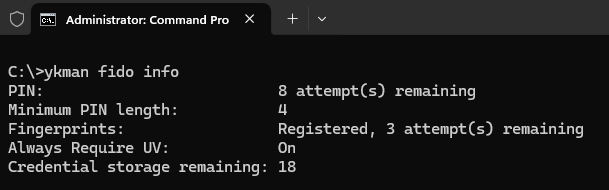
So this command returns general information about the key and for example we can see that there are 18 more credentials that I can store in this key. Because this is from the biometric key we can also see that it always requires user verification upon use, meaning that it requires my biometric and not “plain touch”. Let’s list the accounts next.
I learned that you don’t have to use the –pin option and if you leave it out it will prompt it which would have been better way to go with these screenshots 🙂 So I listed the accounts using the fido credentials list
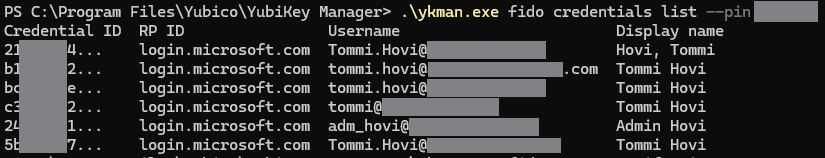
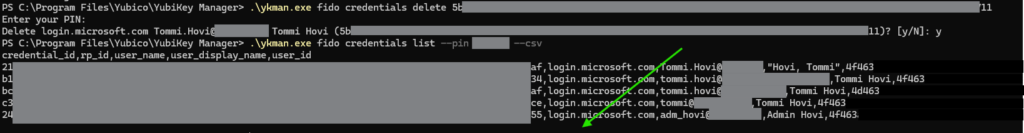
According to the documentation I should be able to manage accounts using Username but I could not get that to work somehow so I used the Credential ID instead, which is a unique value as well. In order to see the whole Credential ID you can use the –csv option. I’m going to remove the account listed at the bottom (highlighted) which ends with ’11’.
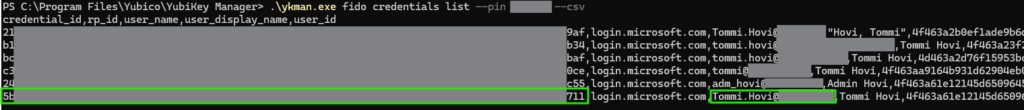
Remove an account
Using the Credential ID let’s target our removal to the last account on the list. Use fido credentials delete command followed by the value of credential id to delete a record. Here you can see that leaving out the pin will prompt it before executing the command. After the delete command I wanted to list again to make sure what I’ve deleted. And sure enough the credential id ending with 11 has been deleted and is no longer in the list.
Managing fingerprints
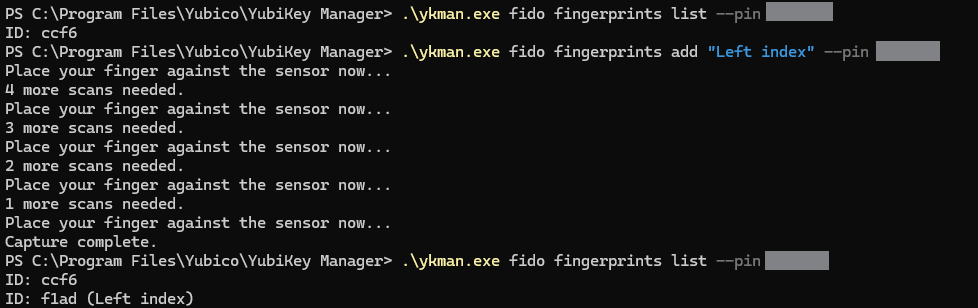
Next I wanted to add another fingerprint to the key. Let’s first list the current fingerprints that we have using the fido fingerprints list command. We only have one with the id of ccf6. Let’s go ahead and register another using fido fingerprints add command. You can add a name for the print as I have here labeled it as “Left index”. Then scan your finger as many times as is needed for the whole print to be covered completely.
Now listing the fingerprints again will show two fingerprints with the new print id and name being f1ad (Left index).
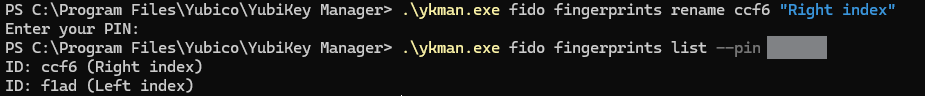
Of course I wanted to name the existing original fingerprint also so I used fido fingerprints rename [id] to rename the ccf6 fingerprint with name of Right index.
Documentation
For complete list of commands like resetting the security key you can find here: FIDO Commands — ykman CLI and YubiKey Manager GUI Guide documentation
YubiKey Manager Desktop App
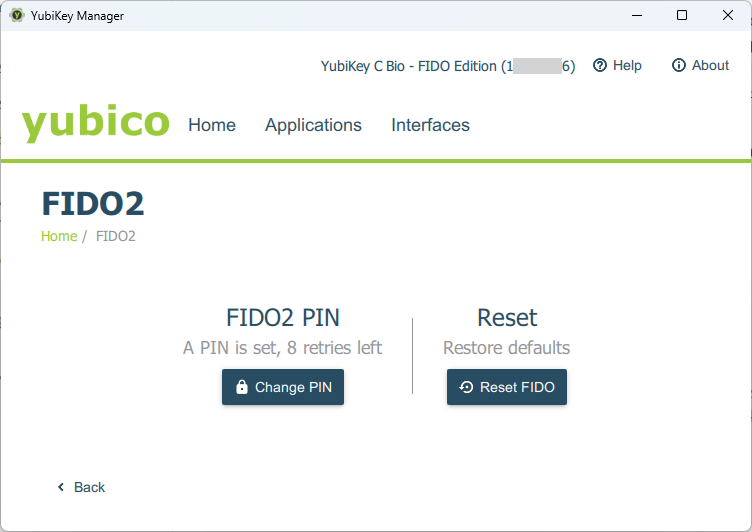
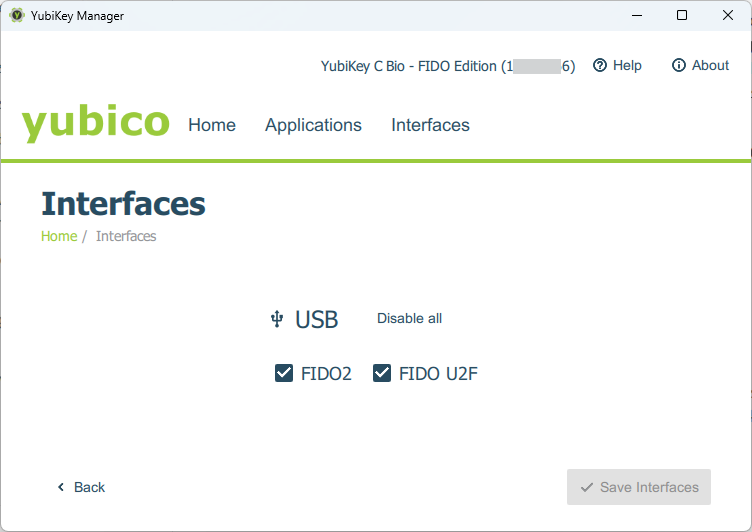
Running the YubiKey Manager desktop app gives you a lightweight control pane for seeing some information about your key like the Serial Number and Firmware version. You can also see the key applications (e.g. I only have FIDO2 in my key), which let’s me change the key PIN or reset the key (both also doable with the ykman CLI). And lastly you can manage your key interfaces. In my case I have FIDO2 and FIDO U2F interfaces enabled. FIDO U2F is Universal Second Factor which an older protocol which FIDO2 expands offering more authentication options like passwordless authentication.
Summary
I can highly recommend using the YubiKey Manager to manage your security key. Installing the tool is easy-peasy, commands are all available in public documentation and any single command is quite easy and intuitive to use with just couple of options that are well documented. This clean-up task and adding the additional fingerprint took me around 15 minutes incl. installation. Just make sure that you have local administrator permissions and you’re good to go!
Stay secure!