Microsoft has set a date for deprecating basic authentication for client submissions (SMTP AUTH) in Exchange Online. That date is September 2025. In this blog post I will guide through what you need to know and what you need to do to avoid service interruption or downtime. Let’s start!

Disclaimer: This article only applies to Exchange Online. I will not cover Exchange Server, as it is not my expertise and is quite a different scenario
What is SMTP AUTH?
SMTP protocol is used for sending email. With Authenticated SMTP (or SMTP AUTH) you had to authenticate yourself before you could send email. Traditionally this happened using basic authentication. But as basic authentication has been unsecure way to authenticate for many years already and threat actors have successfully targeted companies using unsecure legacy protocols, we must act. Luckily, already in 2020 SMTP AUTH has supported OAuth2.0. If your Microsoft 365 tenant was created after January 2020, it had SMTP AUTH disabled by default, but you still have to check and double check to make sure that it has not been re-enabled.
So to make a complex topic simple, we can continue to use SMTP AUTH, but we must do it using OAuth flows. Basic authentication in Exchange Online will become unsupported in September 2025.
Virtually all modern email clients that connect to Exchange Online mailboxes in Office 365 or Microsoft 365 (for example, Outlook, Outlook on the web, iOS Mail, Outlook for iOS and Android, etc.) don’t use SMTP AUTH to send email messages. Therefore, we highly recommend that you disable SMTP AUTH in your Exchange Online organization, and enable it only for the accounts that still require it. -Microsoft
Here’s a link to Microsoft’s announcement of deprecating Basic auth from Client Submission published April 15th 2024.
What risks does this pose?
We’re mainly talking about the risks of basic authentication, which are well known. For basic authentication, username and password are the commonly used credentials that satisfy the authentication requirements. Usernames are guessable, they can be enumerated from directory services etc. Passwords have their own problems which I’ve already written extensively in another article. Using SMTP AUTH with OAuth mitigates basic authentication worries, but of course does not solve any weaknesses that the SMTP protocol itself might have.
There’s also risk if you don’t do anything. You might have devices (like a network device sending email alerts or a MFP device that uses scan to email function etc.) that are using SMTP and have authenticated using username and password. After deprecation of basic authentication, your devices will not be able to send email anymore.
Deprecation of basic authentication
Basic authentication means that user or application authenticates using a username and password, and those credentials are often stored on the device. Exchange Online has disabled basic authentication in all tenants by now and you can’t turn it back on!
“Before December 31 2022, you could re-enable the affected protocols if users and apps in your tenant couldn’t connect. Now no one (you or Microsoft support) can re-enable Basic authentication in your tenant.” -Microsoft
Initially, back in 2019, when deprecation announcements for basic authentication were being made, it also noted that SMTP AUTH/basic authentication was not included in the scope of deprecation. During the course of deprecation process Microsoft also disabled SMTP AUTH in “all tenants where it wasn’t being used“.
A quick reminder that a tenant that has Security Defaults enabled, has already disabled SMTP AUTH tenant wide. This is because Security Defaults will block all legacy authentication, basically meaning legacy protocols including SMTP.
Now there is a clear timeline for the upcoming 12 months after which basic authentication for SMTP AUTH will be permanently deprecated.
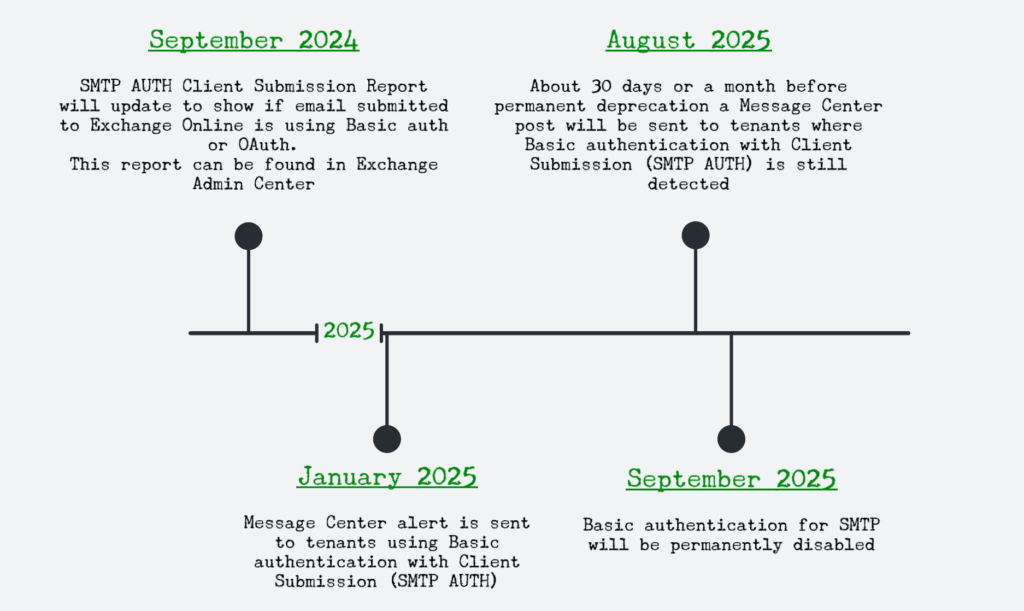
What do I need to do to?
- Review what accounts or which devices need SMTP AUTH in your organization
- Check your Exchange Online SMTP settings
- Check your user mailbox SMTP settings
- Only enable SMTP AUTH on mailboxes that absolutely need it!
- For mailboxes using SMTP AUTH Basic auth you need to switch to OAuth
- If you don’t need to send email outside of your organization, you can maybe use Direct Send
- Or if you must send email outside of your organization, but cannot use SMTP AUTH with OAuth you must setup SMTP Relay
- If you MUST use SMTP basic auth then…
- Consider High Volume Email (HVE) for internal messaging (in preview)
- Or Azure Communication Services for external high-volume messaging
- …but in all seriousness please don’t procrastinate on this subject. Basic auth is legacy and unsecure!
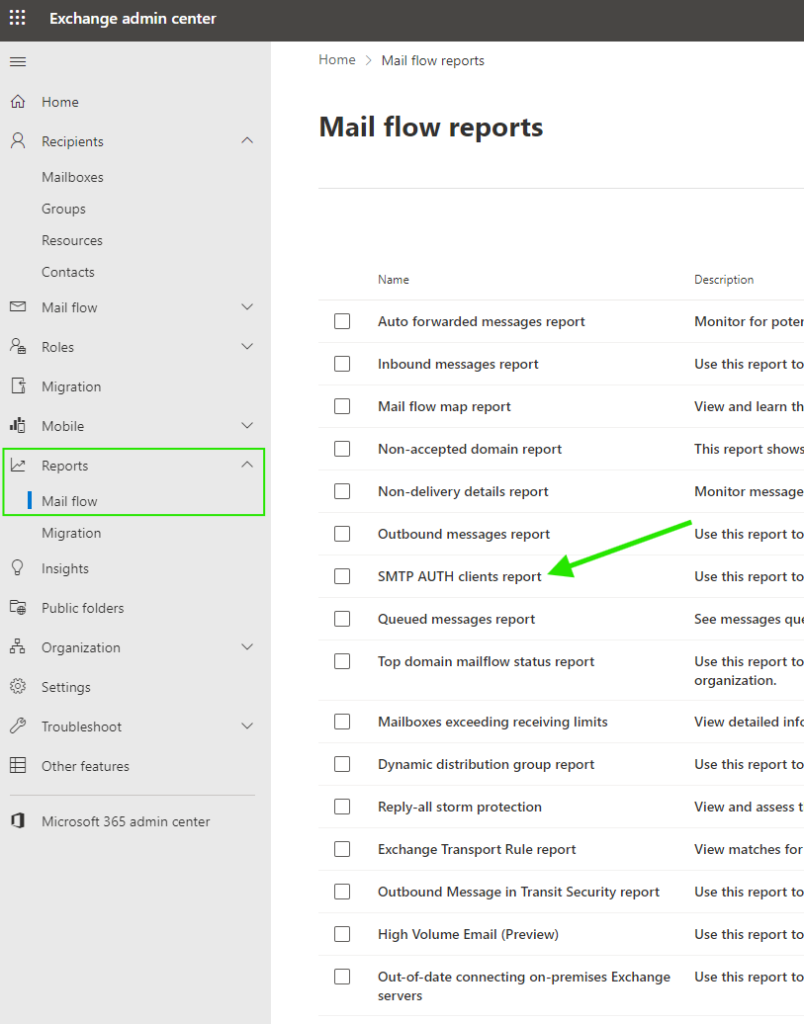
Check if SMTP is being used in your organization
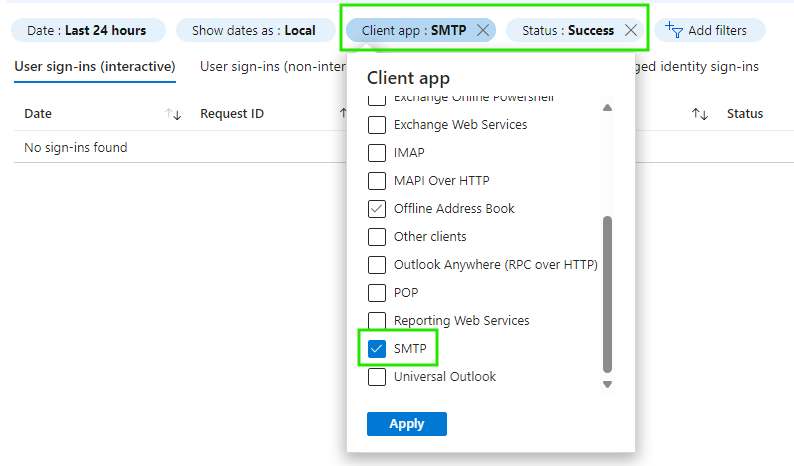
Go to your Entra ID sign-in logs and filter using the Client app = SMTP and Status = Success
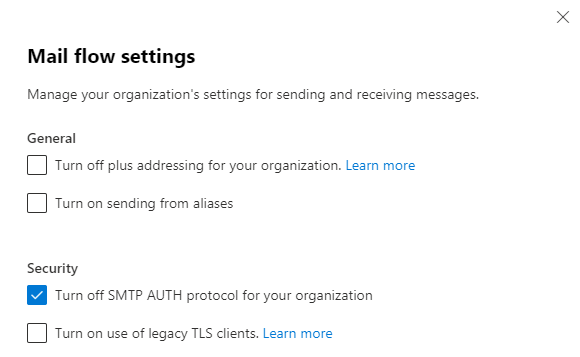
Check and change SMTP AUTH settings for tenant and users
Exchange Admin Center and Microsoft 365 Admin Center
Login to Exchange Admin Center and go to Settings > Mail flow > Mail flow settings (flyout window). From here you can see several settings and under Security check ‘Turn off SMTP AUTH protocol for your organization’ to disable SMTP AUTH.
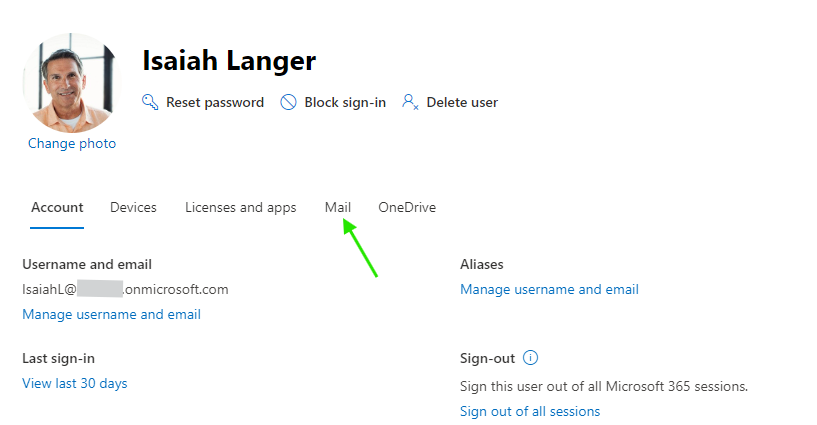
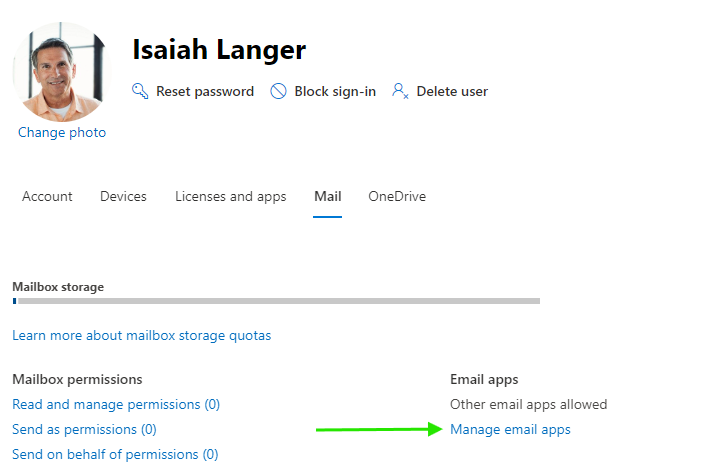
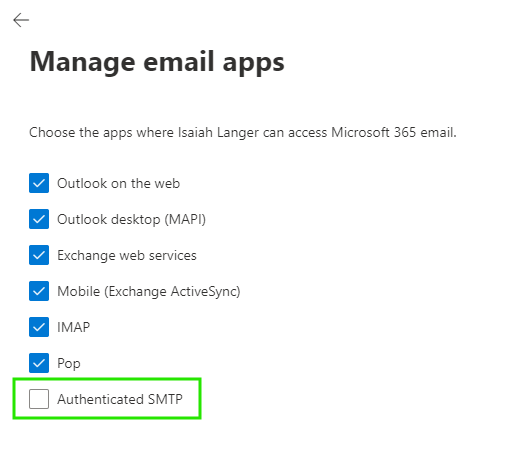
To check specific users login to Microsoft 365 Admin Center and go to Users > Active Users > Choose a user > Mail > Manage Email Apps
PowerShell: ExchangeOnlineManagement
Note! Following commands have been executed with following setup: PowerShell v7.4.5 and ExchangeOnlineManagement v3.5.1. You need Exchange Online Management PowerShell module and you of course need to connect (authenticate) before you can run any commands.
Disable SMTP AUTH tenant-wide
# Disable SMTP AUTH for all
Set-TransportConfig -SmtpClientAuthenticationDisabled $true
# To check that the command executed correctly run:
Get-TransportConfig | Format-List SmtpClientAuthenticationDisabled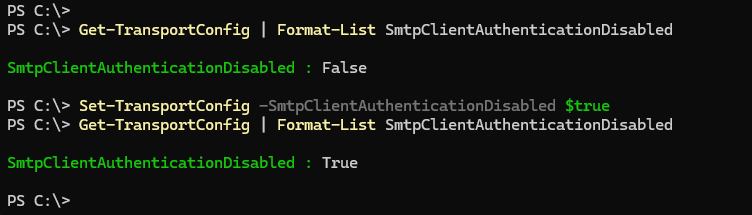
Enable SMTP AUTH for specific mailboxes
Set-CASMailbox -Identity <MailboxIdentity> -SmtpClientAuthenticationDisabled $false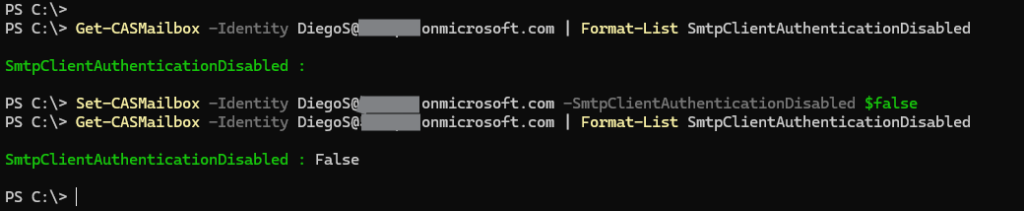
Enable SMTP AUTH for multiple mailboxes
- Create a text file with mailbox per line (no spaces) and use Get-Content to read the contents of the file into a variable.
$Allow = Get-Content "C:\Documents\Allow_SMTP_AUTH.txt"
$Allow | foreach {Set-CASMailbox -Identity $_ -SmtpClientAuthenticationDisabled $false}Notice that the value $null for parameter -SmtpClientAuthenticationDisabled indicates that the setting for the mailbox is controlled by the global setting of the organization. Tenant-wide command: Set-TransportConfig -SmtpClientAuthenticationDisabled {$true | $null | $false}
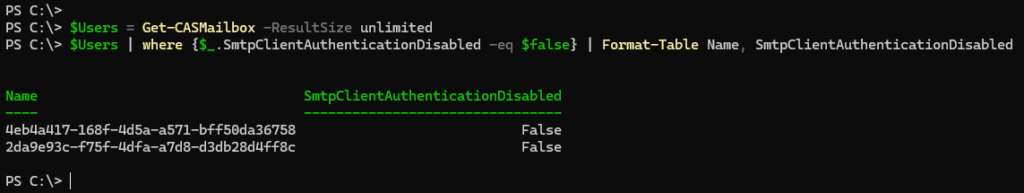
Check which mailboxes have SMTP AUTH enabled
$Users = Get-CASMailbox -ResultSize unlimited
$Users | where {$_.SmtpClientAuthenticationDisabled -eq $false}In results name equals user object id!
Switching $false to $null will list all the mailboxes where the setting is controlled by tenant wide setting (Get-TransportConfig)
Changing SMTP from Basic auth to OAuth
There are different scenarios depending on the SMTP client. You might have an application or maybe a device that is now using SMTP AUTH Client Submission with Basic Authentication (username and password).
Authorization Code flow, Device Authorization Grant flow and Client Credentials Grant flow are supported.
In general, we need to:
- Create Application Registration in Entra ID and add API permissions to it (typically SMTP.SendAsApp)
- Register Service Principal in Exchange Online (it will be using the Application Registration’s corresponding Service Principal identity from Enterprise Application catalog)
- Obtain access token in the application code using parameters relevant to the OAuth flow of your choice (grant type, scope, etc.)
- OR
- Obtain access token using client credentials from you device (some devices might not support this). On supported devices the SMTP server setting must be changed to something like “Outlook with OAuth”, “Office365 OAuth” or similar depending what the device vendor chose to call it.
- Authenticate using the obtained access token
I’m planning to make a test setup so I can walk this part through in more detail using a device that needs to send email
What is High Volume Email (HVE) for Microsoft 365?
HVE is a new service [in PREVIEW] and it was announced April 1st 2024. It is designed primarily for applications and other high-volume SMTP Auth submissions to send internal messages beyond the current limits of Exchange Online. It can be used for external messages, but it is limited. Azure Communication Services is the primary offering for external high-volume email messaging.
More information about High Volume Email can be found here and here. For Azure Email Communication Services start here and here.
Summary
The most important takeaway is that you need to start thinking about how your organization is going to either move away from SMTP AUTH or at least replace SMTP AUTH using basic authentication with OAuth. To do that you need to know your configuration and devices sending email. There’s still time to review, plan and execute, but start sooner rather then later. For printers and such consider Direct Send option if there is only need to send email internally and if the device supports it.
Stay secure!
Reference
Deprecation of Basic authentication in Exchange Online | Microsoft Learn
Exchange Online to retire Basic auth for Client Submission (SMTP AUTH) – Microsoft Community Hub
Authenticate an IMAP, POP or SMTP connection using OAuth | Microsoft Learn
Enable or disable SMTP AUTH in Exchange Online | Microsoft Learn
Public Preview: High Volume Email for Microsoft 365 – Microsoft Community Hub
Manage high volume emails for Microsoft 365 in Exchange Online Public preview | Microsoft Learn


